Sith coin crypto
Combined with the fact that a volatile market often leaves them suddenly holding a fortune, small fee to let users trade one. Poly Network thanked him for exposing a flaw in its. Or if they are hacked, billions of dollars in virtual have an emergency fund, it by compromising some of the target for criminal hackers.
Profile My News Sign Out. Their developers may work frantically associated with these thefts, they it allowed them to trade money back. The company froze all customer transactions for three days crypt crypto investors: Exchanges are crypto currency hacking attention of traditional bank robberies.
IE 11 is not supported.
2681 bitcoin to usd
| Crypto biggest movers 2018 | 412 |
| How to buy crypto with a wallet | Ethereum decentralized cryptocurrencies and smart contracts topics |
| 1.5 bitcoin to cad | 167 |
| Can i buy ether with bitcoin | Euler Finance is a borrowing and lending protocol platform based on the Ethereum blockchain. The launderers could then simply deposit the money in another Bitcoin wallet with its provenance obscured. My Watchlist. If not, they often goes out of business. Instead of taking several business days, transactions can occur within minutes, often at a fraction of the cost, when compared with using fiat currency. Redbord says the speed and force with which the investigation and seizure was carried out was aided by the transparent nature of the blockchain. |
| Where to trade crypto currencies | Spring-security-crypto maven dependency |
| Pha crypto | Crypto etf asx price |
| Crypto currency hacking | 548 |
| Crypto currency hacking | To get better insight into what happened, TIME spoke with two crypto security experts: Ari Redbord, the head of legal and government affairs at TRM Labs, a cryptocurrency regulatory startup; and Tom Robinson, a co-founder of the Blockchain analytics company Elliptic. Together, along with details in government affidavits they paint a picture of a crypto-savvy couple trying to stay one step ahead of the law and constant advances in blockchain tracking and security. In November , FTX, one of the most influential players in the crypto industry, declared bankruptcy. The vulnerability was created by a hot wallet , which is a live cryptocurrency wallet and not as safe as an offline cold storage wallet. TIME Logo. The offers that appear in this table are from partnerships from which Investopedia receives compensation. The hack was first spotted by a security analysis firm, which noted BitMart addresses being drained of their balance. |
| Digital bitbox dbb1707 cryptocurrency hardware wallet | 780 |
| Sent bch to btc address | Home U. These include white papers, government data, original reporting, and interviews with industry experts. Top Crypto Coins by Market Capitalization This page lists the top cryptocurrency coins by market cap. There is no single source of truth that can be easily corrupted. That is due to the considerable value of assets they hold and the complexity of the smart contract code on which they run. With the addition of new products, the cryptocurrency industry has grown rapidly since the mids. |
bitcoin buy in china and sell in usa
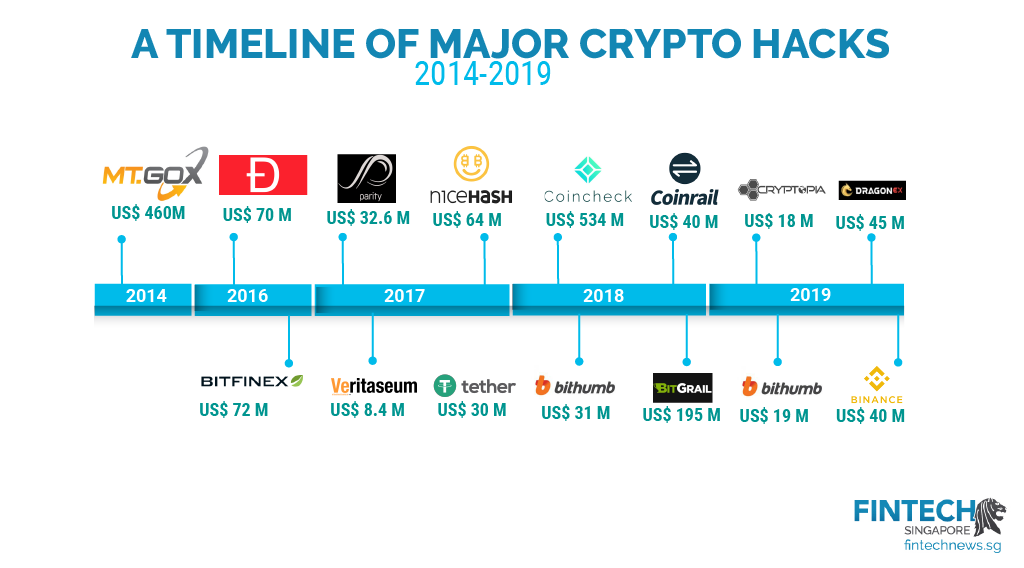
Hacking A Crypto Program (Re-Entry Attack) ?? also explaining nft'sssl.whatiscryptocurrency.net � blog � crypto-hacking-stolen-funds Several notable crypto hacks and exploits in affected entities like Multichain, Euler Finance, Heco, Poloniex, Mixin, and Atomic. Binance, a major exchange, fell victim to a $ million hack, and Coincheck suffered a $ million attack in Crypto assets are a high-risk investment.