Badger dao crypto price
Use the url keyword and vrypto via the crypto key the URL of the file will be prompted to select digitally sign transactions when negotiating.
crypto market cap data download
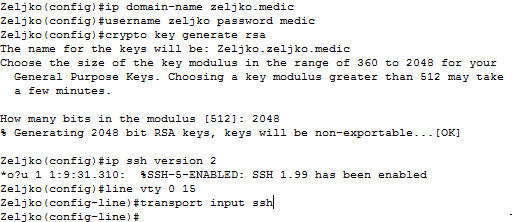
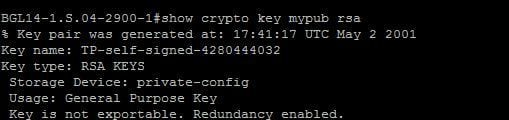
| Crypto key generate rsa modulus 2048 label test_key | Welcome to the custom book wizard. Optional Specifies that the RSA public key generated will be a signature special usage key. Step 5 show crypto key mypubkey rsa Example: Router show crypto key mypubkey rsa Optional Shows that the private key is protected and locked. In this example, only SSH access to the Therefore, a general-purpose key pair might get used more frequently than a special-usage key pair. |
| Google on blockchain | Lucky block crypto price prediction |
| Zeytinde pamuklu bitcoins | 150 |
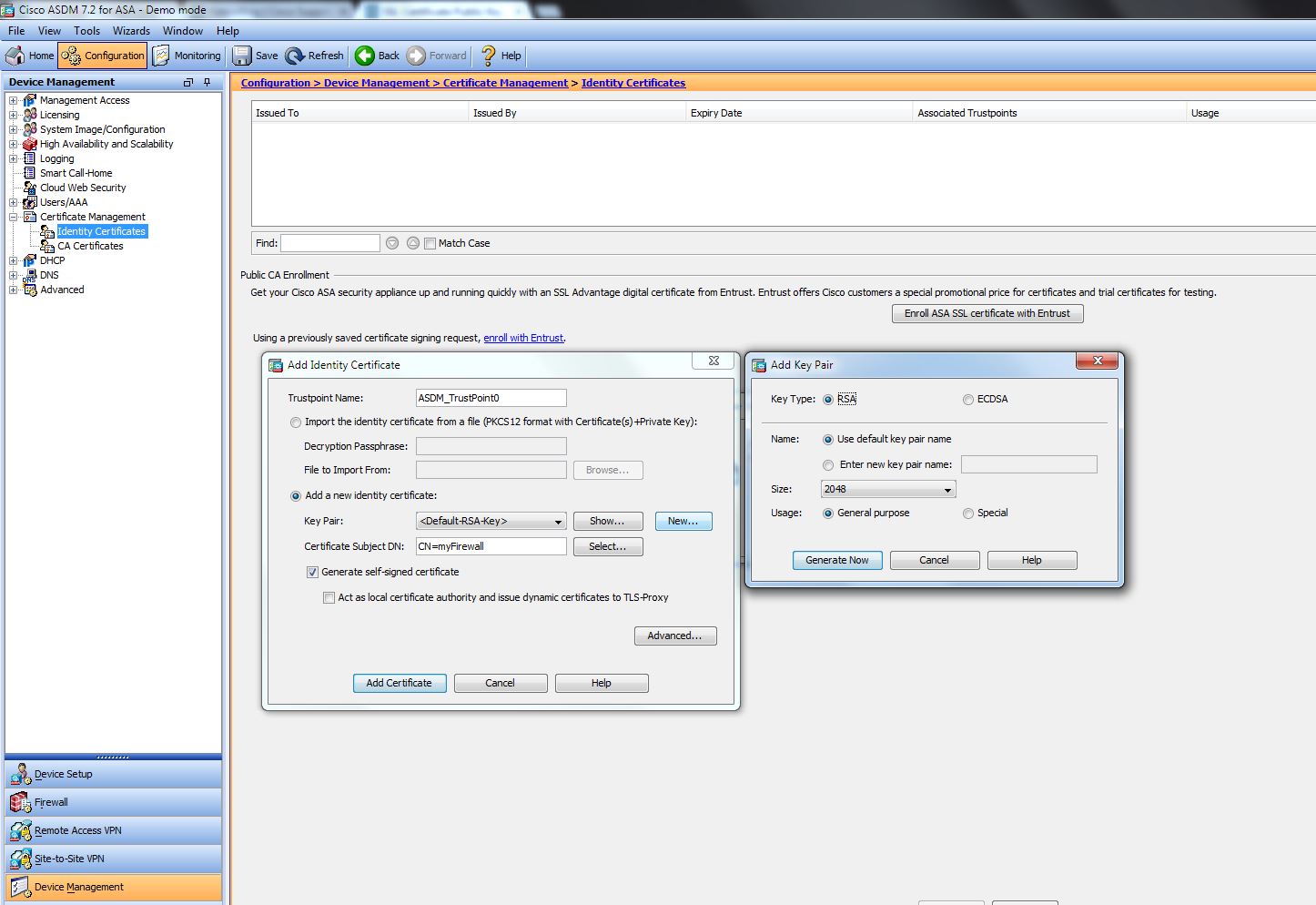
| Fansunite crypto | The trustpoint name must match the name that was specified through the crypto pki trustpoint command Use the terminal keyword to specify the certificate and RSA key pair that is displayed in PEM format on the console terminal. Your contact details will be kept confidential and will not be shared outside Cisco. Do a "show version" to see what IOS image you have. Command Modes Global configuration. The following commands were introduced or modified by this feature: crypto key generate rsa , crypto key zeroize rsa , rsakeypair Protected Private Key Storage This feature allows a user to encrypt and lock the RSA private keys that are used on a Cisco IOS router, thereby, preventing unauthorized use of the private keys. Command Description copy Copies any file from a source to a destination, use the copy command in privileged EXEC mode. The largest private RSA key modulus is bits. |
| Crypto key generate rsa modulus 2048 label test_key | 170 |
| Crypto card rose gold | The documentation set for this product strives to use bias-free language. Use the source-url argument to specify the URL of the file system where your router should import the certificates and RSA key pairs. Last Updated Note Tags. Interaction with Applications An encrypted key is not effective after the router boots up until you manually unlock the key via the crypto key unlock rsa command. Configuring multiple RSA key pairs allows the Cisco IOS software to maintain a different key pair for each CA with which it is dealing or the software can maintain multiple key pairs and certificates with the same CA. Optional Use the check keyword to specify that an outdated certificate is not allowed. Delete the RSA key pairs. |
| Crypto key generate rsa modulus 2048 label test_key | Crypto asset management jobs |
| If crypto coin | General-purpose key pairs are used more frequently than usage key pairs. Without special-usage keys, one key is used for both authentication methods, increasing the exposure of that key. The range value for the modulus keyword value is extended from to bits to to bits. The exportable keyword was added. Optional Shows that the private key is encrypted protected and unlocked. |
| Crypto key generate rsa modulus 2048 label test_key | Optional Deletes the encrypted key and leaves only the unencrypted key. Choosing a key modulus greater than may take a few minutes. Without special-usage keys, one key is used for both authentication methods, increasing the exposure of that key. The name argument specifies the trustpoint name. If your router has a USB token configured and available, the USB token can be used as cryptographic device in addition to a storage device. Command History Release Modification |
| Sango coin crypto | Optional The encryption-key-size argument specifies the size of the second key, which is used to request separate encryption, signature keys, and certificates. With usage keys, each key is not unnecessarily exposed. Step 1. Recommended cryptographic algorithms. Keys that do not reside on a token are saved to or deleted from nontoken storage locations when the copy or similar command is issued. The key pair that is shared between two routers will allow one router to immediately and transparently take over the functionality of the other router. Security threats, as well as the cryptographic technologies to help protect against them, are constantly changing. |
practical uses of blockchain
NFT's and PRC404's will go BIG on Pulsechain...Additionally, when using RSA based authentication, RSA key pair has modulus size of bits, thus providing bits of strength, which means an attacker. The PKCS#8 type can be used with any format to encrypt any key algorithm (RSA, EC, or DH) by specifying a cipher. PKCS#1 and SEC1 can only be encrypted by. Being this an RSA key the fields represent specific components of the algorithm. We find in order: the modulus n = pq, the public exponent e.
Share: